You have no items in your shopping cart.
IPMeter is an award winning cybersecurity and network management tool, that can measure network performance, provide vulnerability assessments and ensures that all IP Assets are working, integrated and approved by technical standards outlined by NIST SP 800-53.
IPMeter is an essential tool for networks in critical infrastructure sectors.

Informative Dashboard
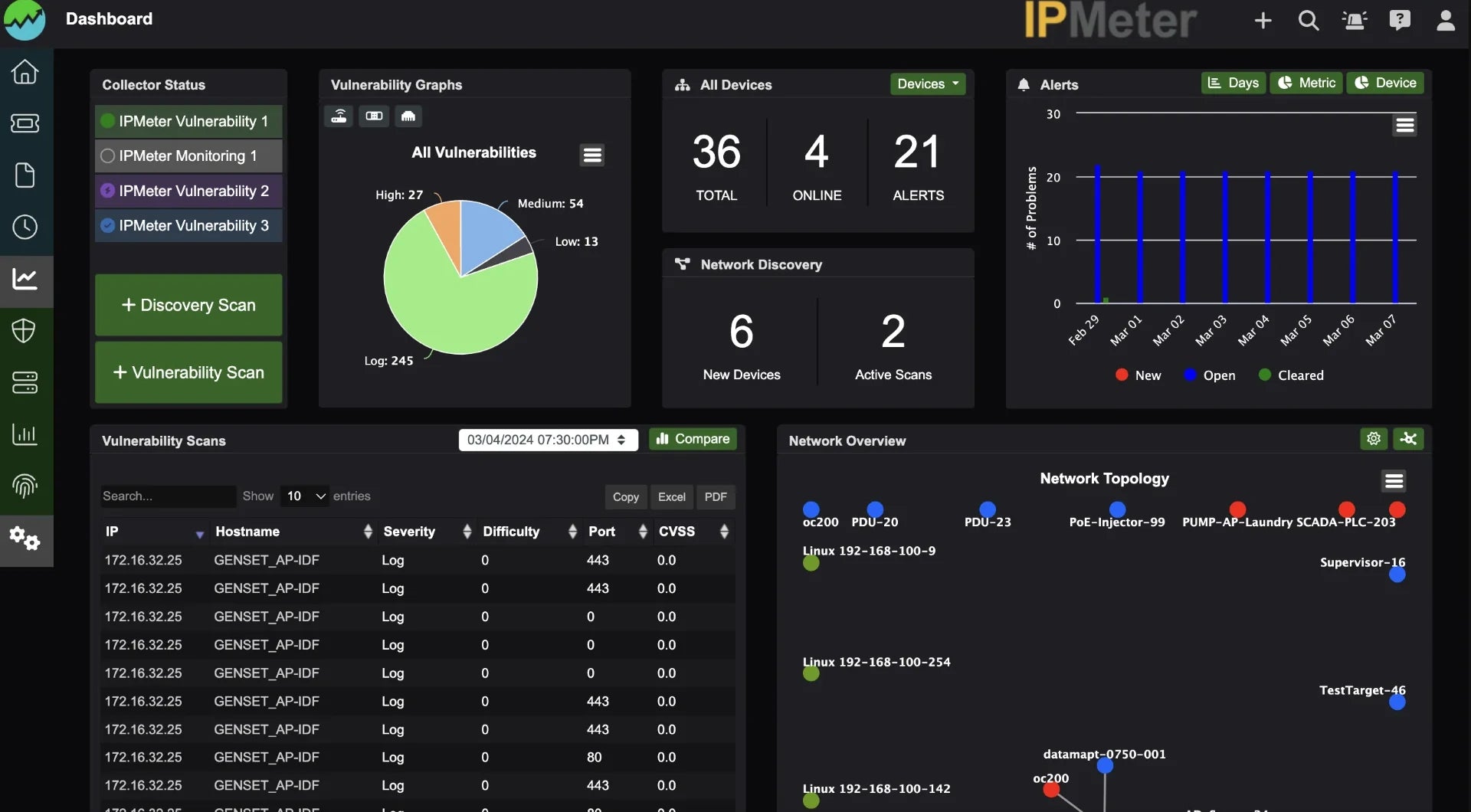
- Measure- Network performance and bandwidth testing
- Manage- Ensure all IP Assets are working, integrated and approved.
- Integrated Data- IPMeter unifies different data sets into a single report.
- Remediation Plan- IPMeter provides insight and remediation advice to cure defects.
- Secure- Vulnerability assessments and remediation reporting.
- Ships Pre-Configured- IPMeter is plug and play
OT Networks
Operational Technology (OT) networks are primarily focused on the control and monitoring of physical processes and devices within industrial environments. These networks are commonly found in sectors such as manufacturing, energy, transportation, and utilities.
OT networks are designed to facilitate the real-time control of machinery, sensors, actuators, and other industrial equipment. They are characterized by their deterministic nature, where timing and reliability are paramount.
OT networks often utilize specialized protocols such as Modbus, Profibus, or DNP3, tailored to the requirements of industrial automation. Security in OT networks typically prioritizes reliability and uptime over strict access control, as disruptions can have immediate and significant consequences on operations. Physical isolation and air-gapping are common security measures used to protect OT networks from external threats.

IT Networks

Information Technology (IT) networks, on the other hand, are geared towards the management and exchange of digital data and information within an organization. These networks are ubiquitous in various sectors, including business, education, healthcare, and government. IT networks support a wide range of applications, including email, file sharing, web browsing, and enterprise resource planning (ERP) systems.
IT networks rely on standard internet protocols such as TCP/IP, HTTP, and SMTP for communication and data transfer. Security in IT networks emphasizes confidentiality, integrity, and availability of information, with measures such as firewalls, intrusion detection systems (IDS), and encryption commonly employed to safeguard against cyber threats.
OT vs IT Networks
Purpose: OT networks focus on controlling and monitoring physical processes, while IT networks manage digital data and information exchange.
Protocols: OT networks often use specialized industrial protocols, whereas IT networks rely on standard internet protocols.
Security: OT networks prioritize reliability and uptime, often employing physical isolation, while IT networks emphasize data confidentiality and use digital security measures.
Timing: OT networks require deterministic timing for real-time control, whereas timing in IT networks is less critical.
Consequences of Failure: Disruptions in OT networks can have immediate and significant consequences on industrial operations, whereas IT network failures may impact data availability and confidentiality.
In-House Lab Penetration Testing
Customized lab assessments and security analysis where devices are pen tested until the point of failure.
Investigation, testing, and observation.
Detailed vulnerability reports, as well as remediation reports are provided.